本文主要涉及Istio学习过程中使用过的一些yaml文件的整理,便于后续作为模板快速拷贝^_^
组件调试
在Istio使用中,遇到被悲催的事莫过于:”配置下发了,但是系统中流量规则始终不生效”(这个直接影响到业务,所以真心要在生产环境中慎用istio)。此时,需要对istio中各组件的工作原理以及其debug方式有一定的了解,下面是一些简单的信息收集方式。
Pilot-Discovery
Pilot启动以后,监听端口 15010(gRPC)和 8080(HTTP)。当应用的Sidecar(Envoy,Istio-Proxy)启动以后,它将会连接 pilot.istio-system:15010,获取初始配置,并保持长连接。
调试方式为:
1 | PILOT=istio-pilot.istio-system:9093 |
这里是代码中对应可以用于调试的URL信息: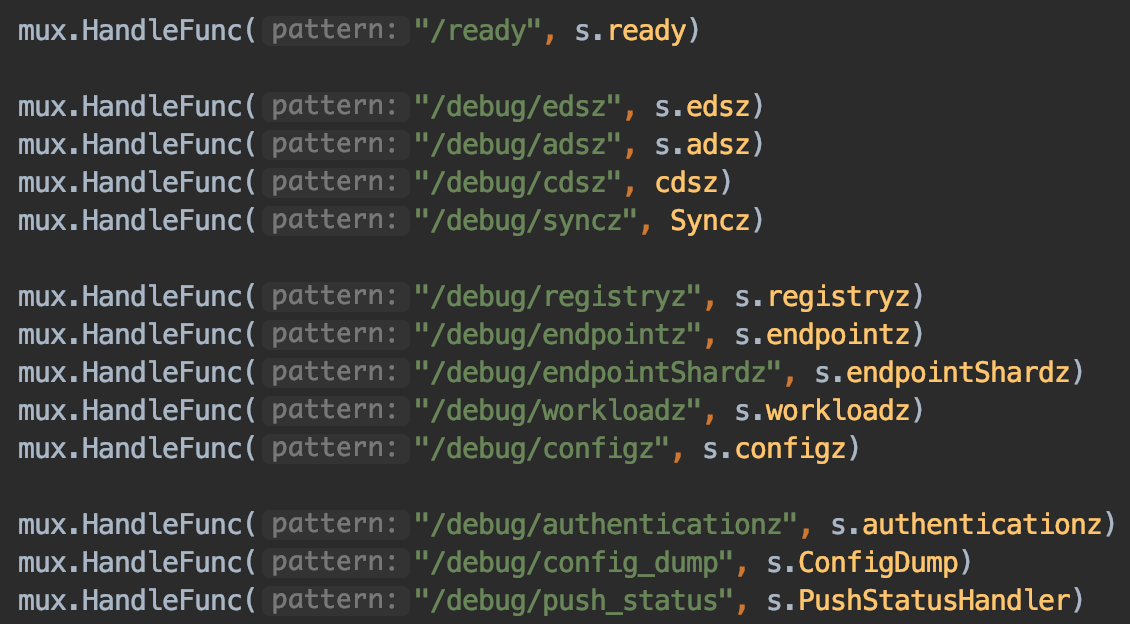
Envoy
Envoy作为客户端,是通过静态配置一个对应的xds server来通过gRPC与server建立长连接并主动获取配置的。对于XDS server这块,有java和golang的control-plane项目,可以实现配置的集中管理。Envoy启动之后,监听 15000 来作为本地的admin端口, 使用15001作为本地的业务端口。
调试的时候,可以通过以下命令来在istio-proxy中获取到动态配置的内容:
1 | curl http://127.0.0.1:15000/config_dump > config_dump |
network.istio.io
主要涉及virtualService,destinationRule,gateway以及serviceEntry这几个概念的理解。
VirtualServices
按权重比例路由
需要结合destinationRule先指定subsets。
1 | apiVersion: networking.istio.io/v1alpha3 |
按HTTP header匹配
http报文header带lab:canary的走v2, 其他走v1
1 | apiVersion: networking.istio.io/v1alpha3 |
按labels路由
基于source service的labels走v2, 其他走v1
1 | apiVersion: networking.istio.io/v1alpha3 |
URI重定向
基于URI做重定向,将”/env/HOSTNAME”替换为对”/env/version”的访问
1 | apiVersion: networking.istio.io/v1alpha3 |
URI重写
基于uri做rewrite, 和redirect不同的是:必须包含route,且不能够和redirect共存
1 | apiVersion: networking.istio.io/v1alpha3 |
超时
1 | apiVersion: networking.istio.io/v1alpha3 |
重试
1 | apiVersion: networking.istio.io/v1alpha3 |
故障注入
1 | apiVersion: networking.istio.io/v1alpha3 |
中断注入
1 | apiVersion: networking.istio.io/v1alpha3 |
mirror
将流量路由到v1,同时,mirror一份到v2。
1 | apiVersion: networking.istio.io/v1alpha3 |
DestinationRules
设置subsets
1 | apiVersion: networking.istio.io/v1alpha3 |
熔断设置
1 | apiVersion: networking.istio.io/v1alpha3 |
Gateway
网关例子
只会接受请求,但不知道路由到哪里,需要配合virtualService来设置。
1 | apiVersion: networking.istio.io/v1alpha3 |
指定路由
virtualService配合gateway路由流量到后端服务。
1 | apiVersion: networking.istio.io/v1alpha3 |
证书支持
- 创建secret文件
1 | kubectl create -n istio-system secret tls istio-ingressgateway-certs --key rocks/key.pem --cert rocks/cert.pem |
- 将secret挂载到/etc/istio/ingressgateway-ca-certs目录
1 | apiVersion: networking.istio.io/v1alpha3 |
virtualService match网关
1 | apiVersion: networking.istio.io/v1alpha3 |
serviceEntry
创建条目
通过hosts来匹配路由,也需要通过virtualService配合。
1 | apiVersion: networking.istio.io/v1alpha3 |
匹配并设置超时
1 | apiVersion: networking.istio.io/v1alpha3 |
config.istio.io
Mixer
Instance: 声明一个模板, 用模板将传给 Mixer 的数据转换为适合特定适配器的输出格式Handler: 声明一个适配器的配置Rule: 将Instance和Handler连接起来,确认处理关系
handler列表
| 名称 | 作用 |
|---|---|
| Denier | 根据自定义条件判断是否拒绝服务 |
| Fluentd | 向Fluentd服务提交日志 |
| List | 用于执行白名单或者黑名单检查 |
| MemQuota | 以内存为存储后端,提供简易的配额控制功能 |
| Prometheus | 为Prometheus提供Istio的监控指标 |
| RedisQuota | 基于Redis存储后端,提供配额管理功能 |
| StatsD | 向StatsD发送监控指标 |
| Stdio | 用于在本地输出日志和指标 |
denier
- handler
1 | apiVersion: "config.istio.io/v1alpha2" |
- instance
1 | apiVersion: "config.istio.io/v1alpha2" |
- rule
1 | apiVersion: "config.istio.io/v1alpha2" |
listchecker
- handler
1 | apiVersion: config.istio.io/v1alpha2 |
- instance
1 | apiVersion: config.istio.io/v1alpha2 |
- rule
1 | apiVersion: "config.istio.io/v1alpha2" |
prometheus
- instance
1 | [root@k8s istio]# kci get metrics |
- handler
1 | [root@k8s istio]# kci get prometheus |
- rules
1 | [root@k8s istio]# kci get rules |
log(stdio)
满足条件的访问日志会被记录到mixer的stdout上面,通过kubectl logs查看。
1 | [root@k8s istio]# kci get logentry |
1 | [root@k8s istio]# kci get stdio |
1 | [root@k8s istio]# kci get rules |
log(fluentd)
需要先在k8s上部署fluentd,并暴露service为fluentd-listener:24224
- handler
1 | apiVersion: config.istio.io/v1alpha2 |
- instance
定义logentry(sleep-log)并应用;
- rule
1 | apiVersion: config.istio.io/v1alpha2 |
